Last week, cryptocurrency exchange Bybit suffered the largest hack in its history, losing approximately $1.5 billion worth of ETH. Initial speculation pointed to security vulnerabilities within Bybit itself, but as the investigation deepened, the truth emerged: the breach was caused by a compromised developer device at Safe, a multi-signature smart contract wallet provider and Bybit’s partner, which led to the tampering of Safe’s front-end.
The Truth Revealed: Safe Front-End Targeted in Supply Chain Attack
According to a joint investigation by Bybit and Safe, the vulnerability stemmed from Safe’s infrastructure, not Bybit’s internal systems.

Safe’s official statement revealed that the North Korean hacker group Lazarus Group infiltrated a Safe developer’s device and injected malicious code into the front-end website “app.safe.global.” This allowed them to bypass multi-signature verification and disguise fraudulent transactions as legitimate approvals. A Verichains investigation report indicated that the malicious code was highly targeted, activating only under specific conditions (such as when operating Bybit accounts) to avoid affecting ordinary users and remain undetected.
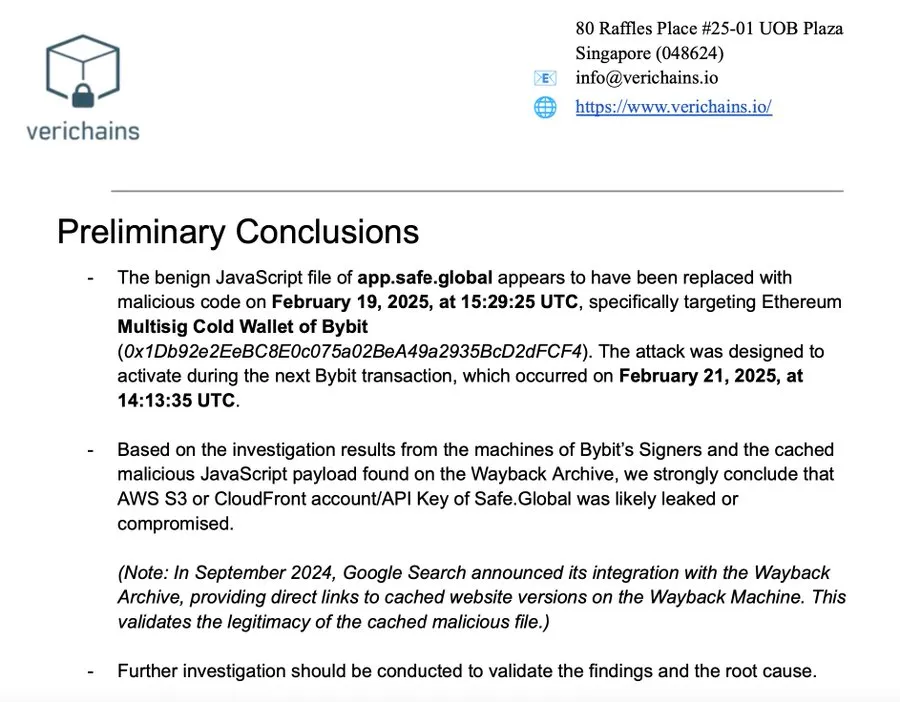
The report further discovered that Safe’s AWS S3, CloudFront accounts, or API keys may have been compromised or stolen, leading to the replacement of front-end files. Cybersecurity expert Yu Xian added that this was a classic supply chain attack:
“The hackers deceived signers through front-end tampering, rather than directly breaching Safe’s smart contracts.”
The Safe team emphasized that external security researchers unanimously confirmed that Safe’s smart contracts themselves were not vulnerable; the issue entirely stemmed from the compromised developer device.
This attack exposed the technical weaknesses of multi-signature wallets and the fatal risks of supply chain attacks, casting doubt on Safe’s reliability as a mainstream security solution in the industry.
Community Reactions: Skepticism, Security Reflections, and Jokes
Yu Xian: Supply Chain Attack Sounds the Alarm
Cybersecurity analyst Yu Xian stated that the malicious code (pointing to the 0xbdd0 address) injected into Safe’s front-end was indeed the key to stealing Bybit’s assets, as confirmed through decompilation.
This aligns with his initial speculation that the attack method could involve Border Gateway Protocol (BGP) hijacking, Domain Name System (DNS) hijacking, or supply chain poisoning, with the latter being confirmed. This resembles the tactics used in the two hacks on Radiant Capital, which lost over $50 million within ten months. He warned that North Korean hackers’ “combination punch” techniques are highly sophisticated:
“All services relying on front-ends or APIs face similar risks, and parties must urgently upgrade their asset management models.”
He also noted that it wouldn’t be surprising if the compromised developer was a North Korean infiltrator.
CZ: Vague Statement Sparks More Questions
Binance founder CZ expressed disappointment with Safe’s statement, criticizing its vague wording for failing to address key questions. He raised five points of concern:
- How was the developer’s device compromised?
- Why did this device have direct access to Bybit accounts?
- How was multi-signature verification bypassed?
- Is $1.5 billion the largest address managed by Safe?
- What lessons can other multi-signature wallets learn from this?
CZ also humorously responded to a community question about whether Binance uses Safe’s services:
“If Binance also used Safe, Bybit might not have been the target.”
Industry Experts: Both Parties Had Clear Shortcomings
Polygon’s Chief Security Officer, Mudit Gupta, questioned why a single developer had the authority to directly modify Safe’s website content without monitoring.
Lido Finance Strategy Advisor Hasu commented:
“Bybit also failed to verify the integrity of transactions on other independent devices when transferring such a large amount of funds, indicating shortcomings in its infrastructure.”
Additionally, analyst AB Kuai.Dong bluntly stated that all small and medium-sized projects using Safe’s services should thank Bybit for becoming the primary target, preventing larger losses. He also noted that Safe’s $100 million funding round, with investor token unlocks just two months away, poses challenges for its future development.
Safe and Bybit Take Active Steps to Remediate
Safe has since taken active measures to address the issue, including rebuilding its infrastructure, replacing credentials, gradually restoring services on the Ethereum mainnet, removing Ledger integration, and adding transaction verification mechanisms.
Meanwhile, Bybit has declared war on Lazarus, launching a bounty program to recover the stolen funds and calling for industry collaboration to combat hackers.
This incident highlights the threat of supply chain attacks to the cryptocurrency ecosystem. Even if smart contracts are secure, front-end and approval processes remain vulnerabilities. For users, caution and multi-layer verification when signing transactions have become the best line of defense.






